Blog


Planning a Hardware Refresh? Turn Retired Devices into Community Impact—Securely

Cyber Resilience Starts Here: How MSPs Protect Essential Services

Cybersecurity Awareness Month: How to Make Your Business Cyber Ready

7 Critical Questions to Ask Before Choosing an IT Security Provider
MSPs and AI: Tools, Best Practices & Pitfalls
The Hidden Dangers of AI at Work: How Misuse Is Undermining Security and Trust

Mid-Year IT Checkup: How MSPs Can Help You Prepare for the Second Half of 2025
Ransomware Defense Strategies: Why Every Business Needs Them and How MSPs Can Help

Embracing the Future of Network Security: What is SASE (Secure Access Service Edge)?

Zero Trust Security: What It Is and Why Your Business Needs It

Data Protection vs. Data Security: How Managed IT Services Protect Your Business

IT Infrastructure: Things to Consider Before Moving Your Office

Best Practices for Protecting Sensitive Data in the Cloud

Protecting Your Business from Cybersecurity Threats: The Importance of IT Managed Services

What to Consider When Hiring an IT-Managed Services Company

Managed IT Services: Once Size Doesn’t Fit All

Why Cloud Migration Services are Important to Small Businesses

Strategic IT Planning for 2025: What to Consider

Essential Role of Data Backup in Protecting Your Business

How to Build an Effective Security Technology Stack: A Comprehensive Guide

Network Support Management: Boosting Security and Performance for Your Business

A Deep Dive into the World of Managed IT Services: Benefits, Challenges, and More

Cybersecurity in the Age of IoT: Safeguarding Your Business Against Emerging Threats

Embracing the Future of Work: How to Effectively Implement Remote Work Infrastructure

Leveraging Artificial Intelligence and Machine Learning for Business Process Automation: A New Horizon in IT Innovation
Cybersecurity Systems

Demystifying Cloud Migration: Everything You Need to Know
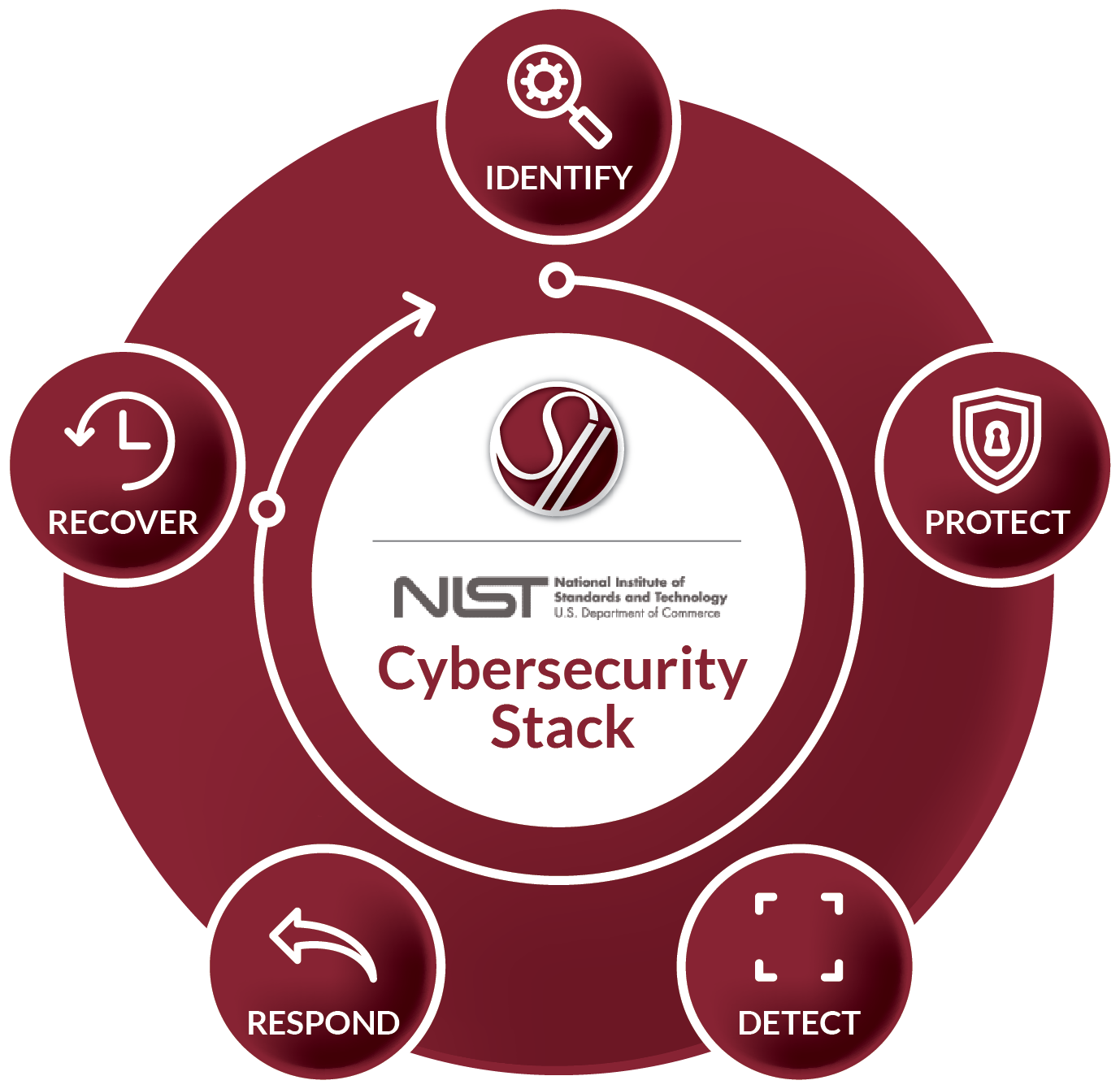
Our New All-Encompassing Security Stack
